As WordPress becomes the Internets preferred Content Management System more and more, the security threats will proliferate more and more! WordPress by itself is already a pretty secure piece of software, but the more you customize it the more vulnerable it is likely to become and even the best security can succumb to massive efforts to break it.
Today Wordfence sent out an alert stating:
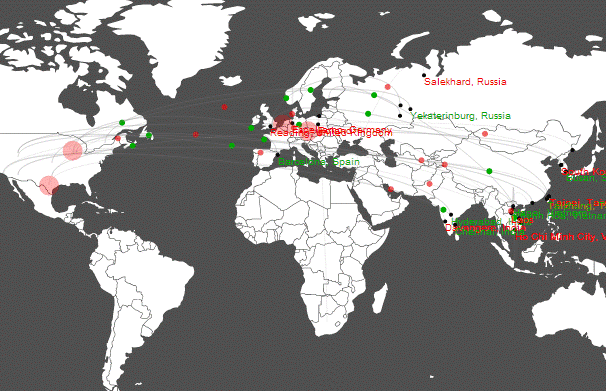
As of 11am eastern time this morning we are monitoring the largest distributed brute force attack on WordPress installations that we’ve seen to date. The real-time attack map onwww.wordfence.com became so busy that we’ve had to throttle the amount of traffic we show down to 4% of actual traffic.
Here you can see a video clip I took from their website showing all of the inbound brute force attacks going into the US.
Immediately I logged into my site and confirmed that my site was being targeted; there were a large number of attempts to login as the Admin to my site. Fortunately I have my site locked down pretty tight and I want to share with you some WordPress security hacks to lock down your site as tight as Fort Knox.
1. Install the Wordfence plugin.
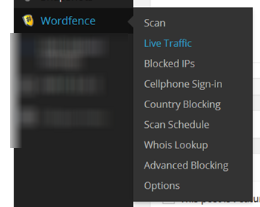 Once you have the plugin installed you can go to WordPress Admin >> Wordfence >> Live Traffic and then choose the “Logins and Logouts” tab at the top. If you watch this page for a little while you may see multiple attempts from all over the world of someone trying to login to your site, that isn’t you. This confirms that you are under attack and need to tack action. You have already taken the first step by installing Wordfence.
Once you have the plugin installed you can go to WordPress Admin >> Wordfence >> Live Traffic and then choose the “Logins and Logouts” tab at the top. If you watch this page for a little while you may see multiple attempts from all over the world of someone trying to login to your site, that isn’t you. This confirms that you are under attack and need to tack action. You have already taken the first step by installing Wordfence.
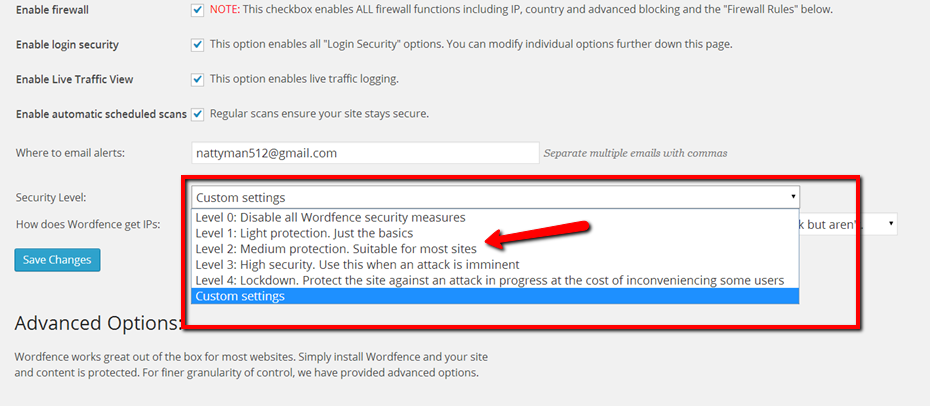
Inside Wordfence go to “Options” and tweak the settings to your desired level of security. The easiest way to do it is just choose one of the preset security levels. I would recommend at least Medium, but if you are experiencing a drag on your site you can go with High or Lockdown.
2. Block Posts That Do Not Come From Your Site
This is my favorite hack, but it is a little more advanced. You will need to edit your .htaccess file with the following code.
### Blocking Spammers Section ###
# Stop protected folders from being hacked and also helps with spammers
ErrorDocument 401 /401.html# Stop spam attack logins and comments
<IfModule mod_rewrite.c>
RewriteEngine On
RewriteCond %{REQUEST_METHOD} POST
RewriteCond %{REQUEST_URI} .(wp-comments-post|wp-login)\.php*
RewriteCond %{HTTP_REFERER} !.*(yourdomain.com).* [OR]
RewriteCond %{HTTP_USER_AGENT} ^$
RewriteRule (.*) http://%{REMOTE_ADDR}/$ [R=301,L]
</ifModule>##############
You can copy and paste that code exactly only update the yourdomain.com to actually use your domain. You will also need to create a 401.html document that says something like “You do not have access to perform this action” and upload it to your server.
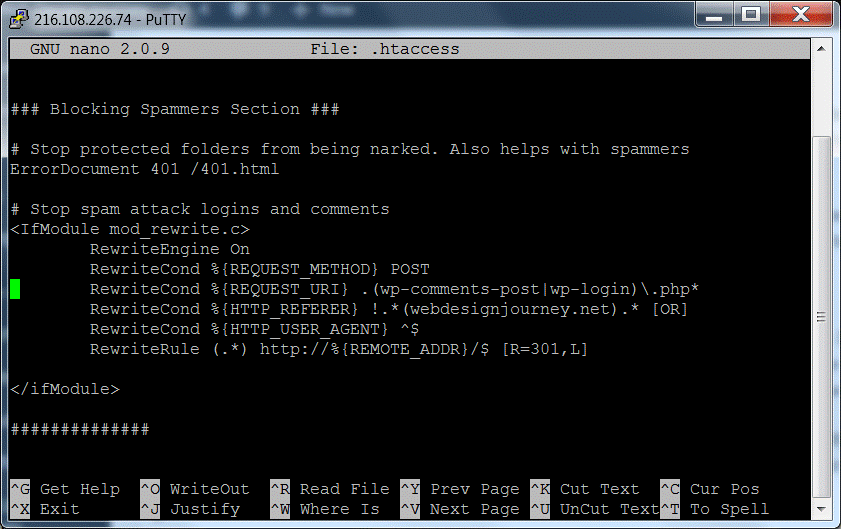
The rest of the script turns on the Apache RewriteEngine, then says if the user is request method is Post, like they are submitting a login form or comment, to either the wp-comments-post.php or wp-login.php AND the originating request does NOT come from your domain or the User Agent is blank, which hackers and spammers leave blank to save bandwidth, THEN redirect the user to their own machine. That last part saves your server resources by not actually having to serve them a webpage.
Pretty stinking awesome!
I had recently commented out that code while I was in the middle of changing my domain. Today after verifying I was getting attacked I un-commented these rules and instantly the bad login attempts stopped in Wordfence as you can see here:
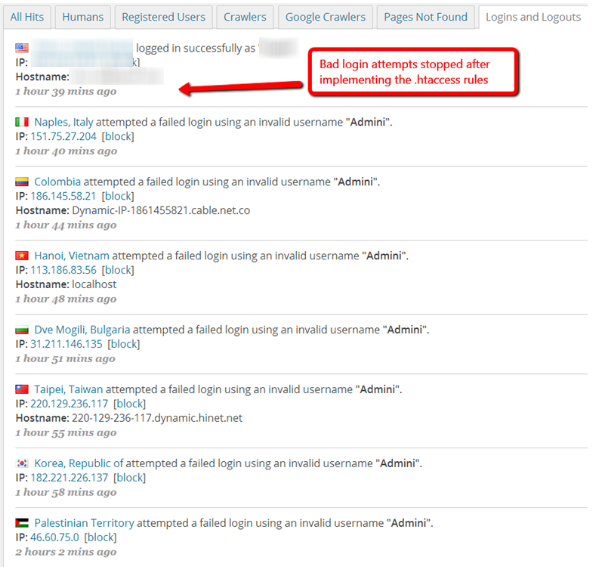
In the above screenshot you can see that every couple of minutes someone was attempting to login from a different country. The top login attempt, which was successful, is me. After that, they didn’t even get far enough to be logged in Wordfence.
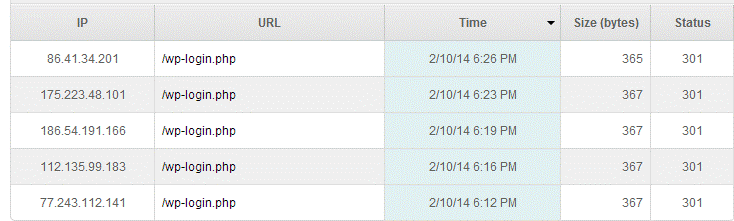
Then looking at my server logs I can see the bad login attempts show up as 301 errors. In other words, I confirmed that they were being stopped in their tracks!
3. Lock Down wp-config.php
Again this is a little more advanced as you will need access to the the server of your website. This trick involves moving the wp-config.php outside of your public folder and making it impossible for anyone but you to ever access.
WordPress is so smart that it will look in more than one place for your wp-config.php file. Most website accounts have the main user account and inside of it the public folder which is available to everyone online. This is usually the /public_html folder or sometimes /www. This is where the root of your website is located.
You need to move the wp-config.php up one folder (or directory) so that it is on the same level as your public_html directory, but not in it. You can easily drag and drop this using FTP or you can use Putty to SSH into your website and follow these commands.
cd /home/your_user_directory/public_html
mv ./wp-config.php ../
Of course make sure the first line uses the actual path to the root of your website, and you should always download a backup of your file before making any changes. Then go to your website in a browser and press CTRL + F5, if you are on a PC, or Command+Shift+R on a Mac, in order to do a “hard refresh,” which clears your cache, to make sure your site is still up. If not, you can undue the last change with “mv ../wp-config.php ./”. If everything is fine, as it should be, go on.
Next you can change the permissions so that only your user has any access to this file. Your FTP client may let you do this by right clicking on the wp-config.php file on your server, and then choose to only allow the owner to have read access and remove all other types of access, but if you are still logged into your account with SSH, from moving the file above, just follow these steps:
cd ../
chmod 400 ./wp-config.php
This moves you up one directory to the new location of your file and makes the file only readable to your account. Since your WordPress installation belongs to your username it still has access, but now no one else will have any way to get to it. Again, go back to your browser and do a hard refresh to make sure your site is okay. You can undue the permission change by typing “chmod 644 ./wp-config.php”
4. Update WordPress and All Plugins and Themes
This is a given. If you are using outdated software it will be more vulnerable to attack. Just like your computers operating system needs to be regularly updated, so does WordPress and all of it’s components. It is also a good idea to go to the home pages of your plugins and themes to see when they were last updated. If it has been more than a year, I would seriously consider finding an alternative that is still being actively developed.
Do NOT make the mistake of thinking that just because WordPress says everything is up to date that you are safe. Some plugins just fall into disrepair and are no longer maintained. Beware, using outdated software may be an open door to the backend of your website.
5. Uninstall any unused Plugin or Themes
Just because a plugin or theme is not activated does not mean that it isn’t vulnerable!! Let me say that again in another way, inactive plugins and themes are still accessible to the outside world because they still reside in a public directory on your website. WordPress components are nearly always stored in the same place, so known vulnerabilities can be easily exploited by simply going to where the component is always located, even if it isn’t active.
I recommend removing all inactive plugins and themes from your site, including default WordPress themes and plugins that you are not using. This means you should only have one (1) theme residing in your WordPress installation at all.
If you think I am being silly I can promise you that, since my website has been up, over 3 years now, I have only been hacked once, and this was how! Like many people do, I tried out a ton of different themes before settling on one, and I did not remove them afterwards. Thankfully I had a good backup (see below). You can read more about my experience of getting hacked and what I learned from it.
6. Update to Secure Passwords
These brute force attacks are hitting your website, most likely, with a dictionary brute force attack where they try the most common passwords on your website and various other combinations over and over until they get lucky. The longer and more complicated your password is, the harder it will be for them to succeed.
If you are using something like “password1” or “qwerty5” or “12345”, then forget it, game over man! You might as well not use a password at all. Never use your name or the name of your website, or anyone’s name for that matter.
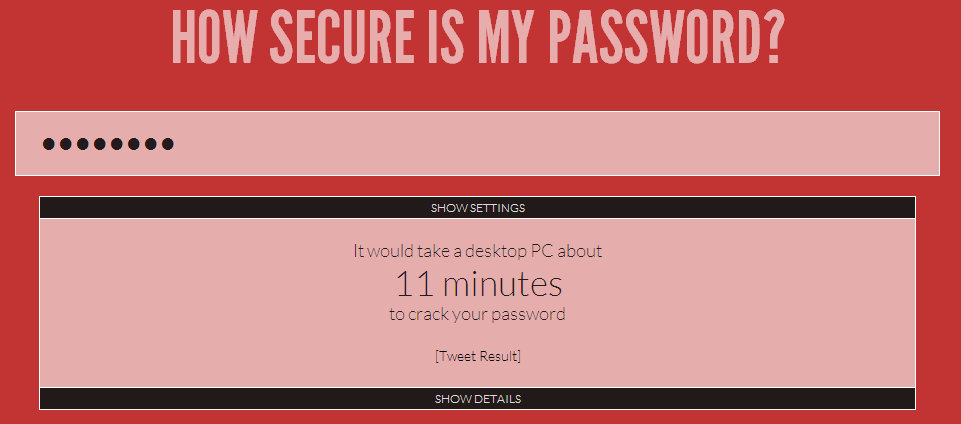
At bare minimum, your passwords should be at least 8 characters long, longer is better. They should include upper and lowercase letters, numbers, and special characters like, !@#$.
Even better are long combinations of 4 unrelated words like “mistertiredrabbitblue”, the key is that the words are not related and don’t make any sense together. That type of password is unbreakable. Add some letters and special characters and a super computer from the future couldn’t touch it.
Here is an awesome tool to see how secure your password is: How Secure Is My Password.
7. Lock Down User Rights
This is simple, if the user that you write content on your website has admin rights then you have just announced to the world half of the user/password combination for complete access to your site. Your authorship user should not be a full admin.
8. Don’t Have an “admin” User
You can name the admin for your site anything, so don’t use “admin” or “administrator” or anything obvious. Making it hard to guess what the username for your admin is, just adds one more hurdle for hackers to overcome.
And obviously, don’t ever author anything with that admin because then it becomes public on your site.
To summarize these last two points, don’t author posts with your admin and don’t let your blog authors have full admin rights. Authors should have Editor or Author rights, keep the two separate.
9. Implement 2 Step Verification
You may have to do this with your bank or Google account already. Whenever I log onto Google from an unfamiliar computer it sends my phone a text with a verification code. There are WordPress plugins that will give you the same ability. It may sound hardcore but it is easier than you think and extremely effective.
The paid version of Wordfence offers 2 step verification, or there are some other plugins you can try like “WordPress 2-step verification”. Here is an article going step by step through setting it up.
10. Backup your website off-server regularly
This may not sound like a security hack, but believe me, when all else fails this is what you want. You must have a regular AUTOMATED backup for your site. Do not rely on manual backups, you may be faithful at first, but eventually the day will come when you realize you haven’t backed up your site for the last month.
Daily backups are good, but make sure you are rotating weekly and even monthly backups too, because here is the dirty secret about hackers… once a good hacker gains access to your site, they will let it sit for weeks before they do anything that would make their presence known. They know that the quickest and most effective way to fix a hacked site is to restore it from a backup. The first thing many website owners do is restore last nights backup, but this won’t do any good if they have already been in your site for a week.
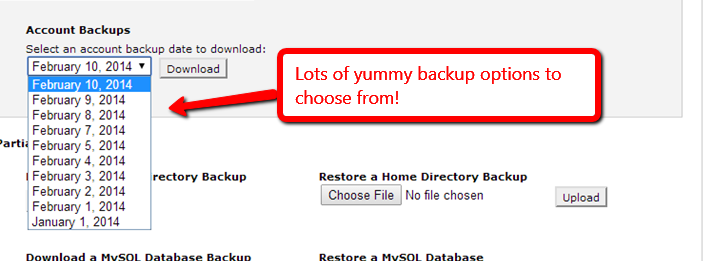
There are many WordPress plugins to backup your site, but make sure your your entire web account is being backed up at the server level. If you are on Cpanel, you can log into your Cpanel admin, and under the Files section go to Backups. There you will find a drop down with all of your available backups, if you don’t have any… better get that fixed before your are hacked.
It is not a question of if someone will try to hack into your website, but when. Likely, someone has tried in the amount of time it took you to read this article. Bot’s are constantly scanning the net, looking for vulnerabilities and indexing WordPress sites to initiate brute force attacks. Don’t wait until your website has been compromised. Don’t assume that it is small and no one will ever notice it, you will be very surprised if you do.
I welcome any comments, questions or recommendations in the discussion area below.